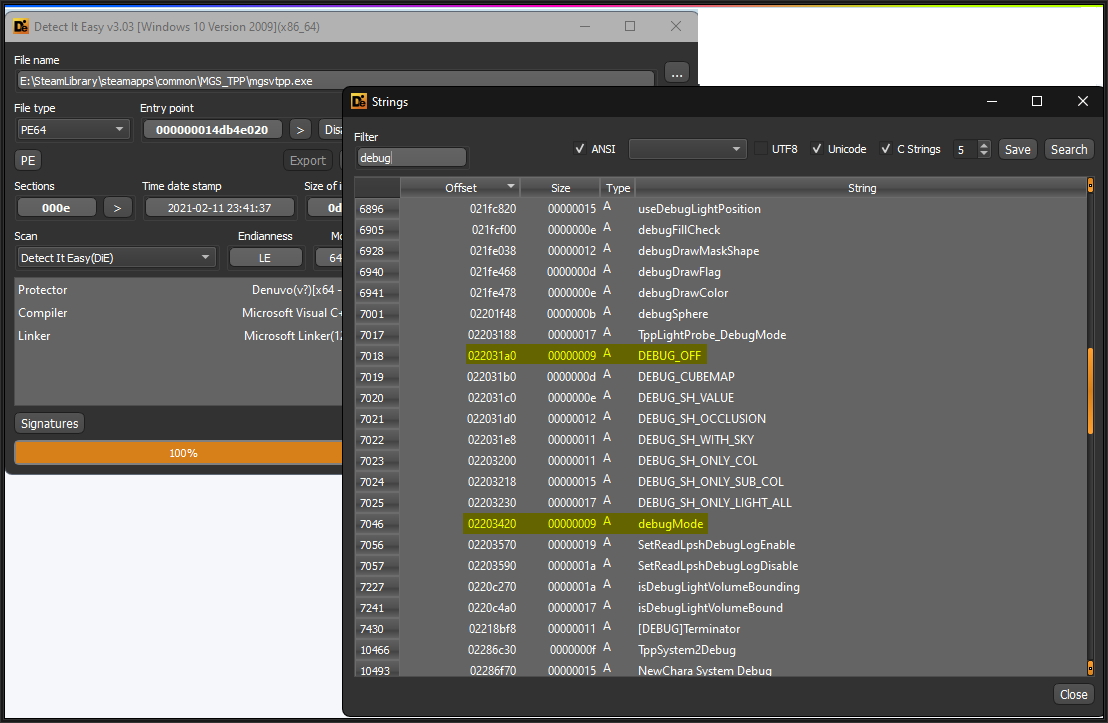
There are also strings for MB Coins such as: MB_COIN, is_mbcoin_dlc, isValidMbCoin, and many more:
Spoiler
Code: Select all
MB_COIN
EULA_COIN_TEXT
EULA_COIN
ERR_MBCOIN_SHORTAGE
use_mb_coin
mb_coin_pay
mb_coin
CMD_GET_MBCOIN_REMAINDER
payment_coin
paid_coin
coin_quantity
remaining_coin
is_mbcoin_dlc
dev_coin
<I=G=MB_COIN>
isValidMbCoin
POOL_REWARD_TYPE_MB_COINthese strings such as dev_coin or isValidMbCoin can be used to give yourself MB coins but since that is serversided I have no idea how.
Strings such as DEBUG_OFF and debugMode are present if you scan for strings, has anyone in the past tried to enable such thing? There are also a bunch of CMD commands that can be viewed here:
Spoiler
Code: Select all
CMD_ABORT_MOTHER_BASE
CMD_ACTIVE_SNEAK_MOTHER_BASE
CMD_ADD_FOLLOW
CMD_APPROVE_STEAM_SHOP
CMD_AUTH_STEAMTICKET
CMD_CALC_COST_FOB_DEPLOY_REPLACE
CMD_CALC_COST_TIME_REDUCTION
CMD_CANCEL_COMBAT_DEPLOY
CMD_CANCEL_COMBAT_DEPLOY_SINGLE
CMD_CANCEL_SHORT_PFLEAGUE
CMD_CHECK_CONSUME_TRANSACTION
CMD_CHECK_DEFENCE_MOTHERBASE
CMD_CHECK_SERVER_ITEM_CORRECT
CMD_CHECK_SHORT_PFLEAGUE_ENTERABLE
CMD_COMMIT_CONSUME_TRANSACTION
CMD_CONSUME_RESERVE
CMD_CREATE_NUCLEAR
CMD_CREATE_PLAYER
CMD_DELETE_FOLLOW
CMD_DELETE_TROOPS_LIST
CMD_DEPLOY_FOB_ASSIST
CMD_DEPLOY_MISSION
CMD_DESTRUCT_NUCLEAR
CMD_DESTRUCT_ONLINE_NUCLEAR
CMD_DEVELOP_SERVER_ITEM
CMD_DEVELOP_WEPON
CMD_ELAPSE_COMBAT_DEPLOY
CMD_ENTER_SHORT_PFLEAGUE
CMD_EXCHANGE_FOB_EVENT_POINT
CMD_EXCHANGE_LEAGUE_POINT
CMD_EXCHANGE_LEAGUE_POINT2
CMD_EXTEND_PLATFORM
CMD_GDPR_CHECK
CMD_GET_ABOLITION_COUNT
CMD_GET_CAMPAIGN_DIALOG_LIST
CMD_GET_CHALLENGE_TASK_REWARDS
CMD_GET_CHALLENGE_TASK_TARGET_VALUES
CMD_GET_COMBAT_DEPLOY_LIST
CMD_GET_COMBAT_DEPLOY_RESULT
CMD_GET_CONTRIBUTE_PLAYER_LIST
CMD_GET_DAILY_REWARD
CMD_GET_DEVELOPMENT_PROGRESS
CMD_GET_ENTITLEMENT_ID_LIST
CMD_GET_FOB_DAMAGE
CMD_GET_FOB_DEPLOY_LIST
CMD_GET_FOB_EVENT_DETAIL
CMD_GET_FOB_EVENT_LIST
CMD_GET_FOB_EVENT_POINT_EXCHANGE_PARAMS
CMD_GET_FOB_NOTICE
CMD_GET_FOB_PARAM
CMD_GET_FOB_REWARD_LIST
CMD_GET_FOB_STATUS
CMD_GET_FOB_TARGET_DETAIL
CMD_GET_FOB_TARGET_LIST
CMD_GET_INFORMATIONLIST2
CMD_GET_LEAGUE_RESULT
CMD_GET_LOGIN_PARAM
CMD_GET_MBCOIN_REMAINDER
CMD_GET_NEXT_MAINTENANCE
CMD_GET_ONLINE_DEVELOPMENT_PROGRESS
CMD_GET_ONLINE_PRISON_LIST
CMD_GET_OWN_FOB_LIST
CMD_GET_PAY_ITEM_LIST
CMD_GET_PF_DETAIL_PARAMS
CMD_GET_PF_POINT_EXCHANGE_PARAMS
CMD_GET_PLATFORM_CONSTRUCTION_PROGRESS
CMD_GET_PLAYERLIST
CMD_GET_PLAYER_PLATFORM_LIST
CMD_GET_PREVIOUS_SHORT_PFLEAGUE_RESULT
CMD_GET_PURCHASABLE_AREA_LIST
CMD_GET_PURCHASE_HISTORY
CMD_GET_PURCHASE_HISTORY_NUM
CMD_GET_RANKING
CMD_GET_RENTAL_LOADOUT_LIST
CMD_GET_RESOURCE_PARAM
CMD_GET_SECURITY_INFO
CMD_GET_SECURITY_PRODUCT_LIST
CMD_GET_SECURITY_SETTING_PARAM
CMD_GET_SERVER_ITEM
CMD_GET_SERVER_ITEM_LIST
CMD_GET_SHOP_ITEM_NAME_LIST
CMD_GET_SHORT_PFLEAGUE_RESULT
CMD_GET_SNEAK_TARGET_LIST
CMD_GET_STEAM_SHOP_ITEM_LIST
CMD_GET_SVRLIST
CMD_GET_SVRTIME
CMD_GET_TROOPS_LIST
CMD_GET_URLLIST
CMD_GET_WORMHOLE_LIST
CMD_MINING_RESOURCE
CMD_NOTICE_SNEAK_MOTHER_BASE
CMD_OPEN_STEAM_SHOP
CMD_OPEN_WORMHOLE
CMD_PURCHASE_FIRST_FOB
CMD_PURCHASE_FOB
CMD_PURCHASE_NUCLEAR_COMPLETION
CMD_PURCHASE_ONLINE_DEPLOYMENT_COMPLETION
CMD_PURCHASE_ONLINE_DEVELOPMENT_COMPLETION
CMD_PURCHASE_PLATFORM_CONSTRUCTION
CMD_PURCHASE_RESOURCES_PROCESSING
CMD_PURCHASE_SECURITY_SERVICE
CMD_PURCHASE_SEND_TROOPS_COMPLETION
CMD_PURCHASE_WEPON_DEVELOPMENT_COMPLETION
CMD_RELOCATE_FOB
CMD_RENTAL_LOADOUT
CMD_REQAUTH_HTTPS
CMD_REQAUTH_SESSIONSVR
CMD_REQUEST_RELIEF
CMD_RESET_MOTHER_BASE
CMD_SALE_RESOURCE
CMD_SEND_BOOT
CMD_SEND_DEPLOY_INJURE
CMD_SEND_HEARTBEAT
CMD_SEND_IPANDPORT
CMD_SEND_MISSION_RESULT
CMD_SEND_NUCLEAR
CMD_SEND_ONLINE_CHALLENGE_TASK_STATUS
CMD_SEND_SNEAK_RESULT
CMD_SEND_SUSPICION_PLAY_DATA
CMD_SEND_TROOPS
CMD_SET_CURRENTPLAYER
CMD_SET_SECURITY_CHALLENGE
CMD_SNEAK_MOTHER_BASE
CMD_SPEND_SERVER_WALLET
CMD_START_CONSUME_TRANSACTION
CMD_SYNC_EMBLEM
CMD_SYNC_LOADOUT
CMD_SYNC_MOTHER_BASE
CMD_SYNC_RESET
CMD_SYNC_RESOURCE
CMD_SYNC_SOLDIER_BIN
CMD_SYNC_SOLDIER_DIFF
CMD_UPDATE_SESSION
CMD_USE_PF_ITEM
CMD_USE_SHORT_PF_ITEM but since I can't find console strings, I have no idea how you would enable such thing. Due to this game being old, maybe someone here has experience so that's why I created this thread.
but since I can't find console strings, I have no idea how you would enable such thing. Due to this game being old, maybe someone here has experience so that's why I created this thread.Also, the game can tell if you have a debugger attached:
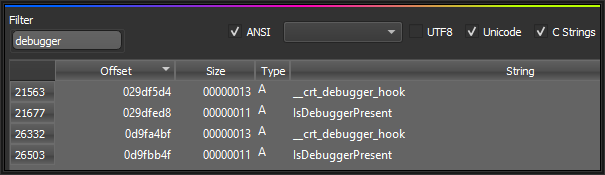
Full list of strings with offset can be viewed here in attachments (password to open: mgsv): Thank you for anyone who supports me in this and looks at it as well!
EDIT: I forgot to mention that I have IDA PRO and currently analyzing the game. Once the analyze is complete, ill upload the snapshot here for people to look at if they have IDA PRO as well.
EDIT 2: IDA scan + strings can be downloaded here (password to open URL + file is mgsv): [Link]
