@VampTY: thanks for your clarification

an image says more than words.
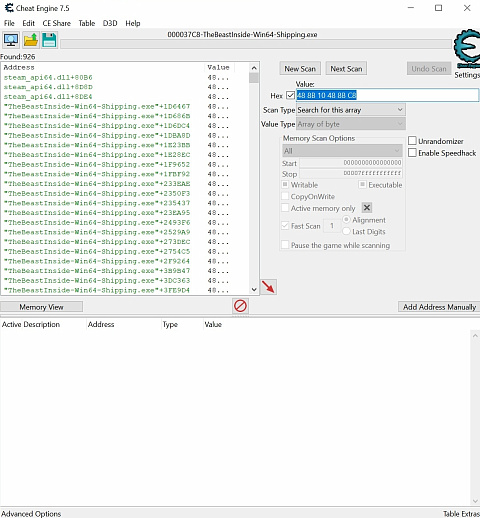
Wow, impressive result... not sure why I had only one

926 vs one is crazy...
Anywy, when having several results, which happens often, we can do two things to narrow the result list. First one is to add addional bytes, just steal them from the code of the script the original author provided. In the code we see that after our search pattern there is a "ff 92 68 05 00 00" coming, just add the ff or ff 92 the the bytes you search for.
Code: Select all
TheBeastInside-Win64-Shipping.exe+83D1C7: 74 29 - je TheBeastInside-Win64-Shipping.exe+83D1F2
TheBeastInside-Win64-Shipping.exe+83D1C9: 48 85 C0 - test rax,rax
TheBeastInside-Win64-Shipping.exe+83D1CC: 74 24 - je TheBeastInside-Win64-Shipping.exe+83D1F2
// ---------- INJECTING HERE ----------
TheBeastInside-Win64-Shipping.exe+83D1CE: 48 8B 10 - mov rdx,[rax]
// ---------- DONE INJECTING ----------
TheBeastInside-Win64-Shipping.exe+83D1D1: 48 8B C8 - mov rcx,rax
TheBeastInside-Win64-Shipping.exe+83D1D4: FF 92 68 05 00 00 - call qword ptr [rdx+00000568]
TheBeastInside-Win64-Shipping.exe+83D1DA: 84 C0 - test al,al
After narrowing down the addresses to only a few possible targets, I usually select the first address which is in the memory of the game, meaning address starts witrh "TheBeastInside" and press Ctrl-D, so I'll see the disassembled code at his very location.
Don't worry, you dont' really need to know assember for this - just narrow down your view to the instructions above and below. In this specific case:
we searched for the 48 8b 10 - meaning mov rdx,[rax]. compare the instructions , walking up from that, just remember "above the mov we have a 'je', 'test', 'je' and below the mov is 'mov', 'call' and 'test'.
Usually this will filter out most if not all other addresses.
Instead of fixing the table every time, we shoud perhaps use the aobcan command to automatically search the right location.

have fun,
Marc